Attackers are actively scanning and exploiting a pair of security flaws (CVE-2024-3272 and CVE-2024-3273) that are said to affect as many as 92,000 internet-exposed D-Link network-attached storage (NAS) devices.
- CVE-2024-3272 (CVSS 9.8):
- This vulnerability has created a backdoor account that an attacker can enable by encoding credentials in the firmware.
- It affects D-Link devices, specifically the models DNS-320L, DNS-325, DNS-327L, and DNS-340L .
- CVE-2024-3273 (CVSS 7.3):
- The same vulnerability affects the D-Link device models mentioned earlier.
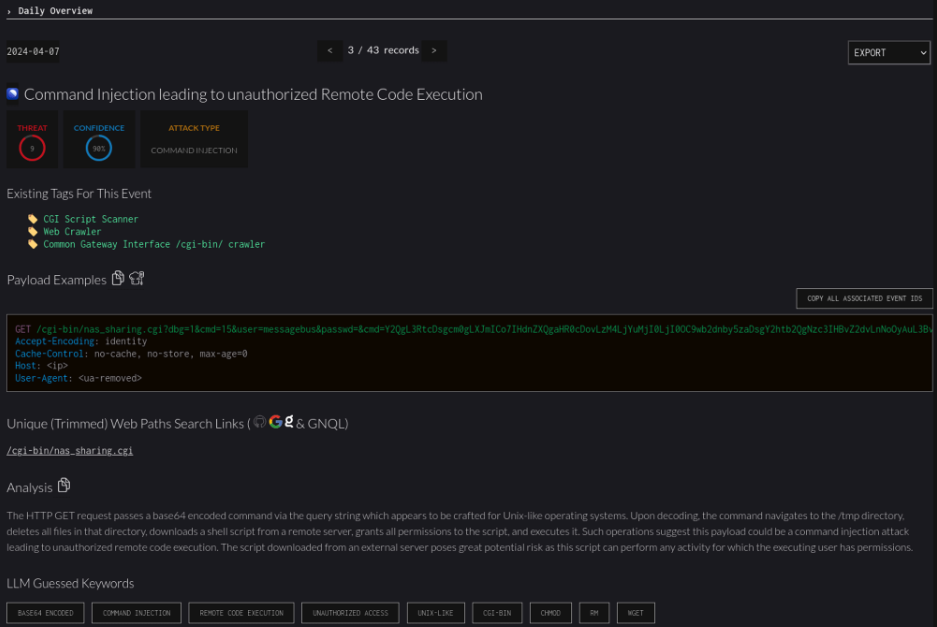
- The vulnerability exists in an unknown function of the file /cgi-bin/nas_sharing.cgi within the HTTP GET Request Handler component.
- It allows for command injection .
Attackers are actively exploiting these vulnerabilities to steal sensitive information, execute arbitrary commands remotely, and orchestrate denial-of-service (DoS) attacks.
It’s crucial for affected users to take steps to protect their devices and apply necessary security updates.
Protecting your D-Link device agaisnt CVE-2024-3272 and CVE-2024-3273
To protect your D-Link device and mitigate the vulnerabilities:
- Update the Firmware:
- Check if there are firmware updates available for your specific D-Link device model.
- Visit the official D-Link website and look for the latest firmware versions for your device.
- Download and install the latest security updates. These typically include fixes for known vulnerabilities.
- Change Default Credentials:
- Ensure that the default administrator and user passwords are modified.
- Create strong and unique passwords to prevent unauthorized access.
- Restrict Remote Access:
- If you don’t need remote access to the device, disable this feature.
- If necessary, configure remote access securely using VPN or two-factor authentication (2FA).
- Control Physical Access:
- Keep the device in a secure location and restrict physical access to authorized individuals.
- Keep the device in a secure location and restrict physical access to authorized individuals.
- Monitor Network Traffic:
- Use network monitoring tools to detect suspicious activities.
- Investigate and take action if you observe unusual traffic or unauthorized access attempts.
- Consider an Additional Firewall:
- Add a network firewall between your D-Link device and the Internet connection.
- This will provide an extra layer of security.
Models affected by the Vulnerabilities
The models affected by this trio of vulnerabilities are:
- DNS-320L
- DNS-325
- DNS-327L
- DNS-340L
If you have any of these devices, it’s important to take measures to protect them and apply necessary security updates.
CVE-2024-3272 and CVE-2024-3273 Solution – No patches available
Unfortunately, there are no patches available for the vulnerabilities CVE-2024-3272 and CVE-2024-3273 in the affected D-Link devices. These vulnerabilities are actively exploited by attackers to take remote control of D-Link network-attached storage (NAS) devices. Approximately 92,000 devices are vulnerable to these remote takeover exploits, which can be transmitted remotely via malicious commands over HTTP traffic.
To protect your devices, I recommend taking the following measures:
Verify Your Device:
- Visit the official D-Link website and verify whether your NAS model is affected.
- Confirm whether your device appears on the list of affected devices.
Update Urgently:
- If your device is on the affected list, download and install the latest firmware update as soon as possible.
- Even though official patches are not available, keep your device up-to-date with the latest versions.
Change Default Passwords:
- Ensure you modify default administrator and user credentials.
- Use strong and unique passwords to prevent unauthorized access


