In the realm of cybersecurity, vigilance is paramount. As we navigate the digital landscape, threats lurk in the shadows, waiting to exploit vulnerabilities within our systems. One such vulnerability that has recently come to light is CVE-2024-3094, a critical flaw impacting the XZ Utils data compression library. But what exactly is CVE-2024-3094, and how does it affect your system? Let’s delve into the details.
Unveiling CVE-2024-3094
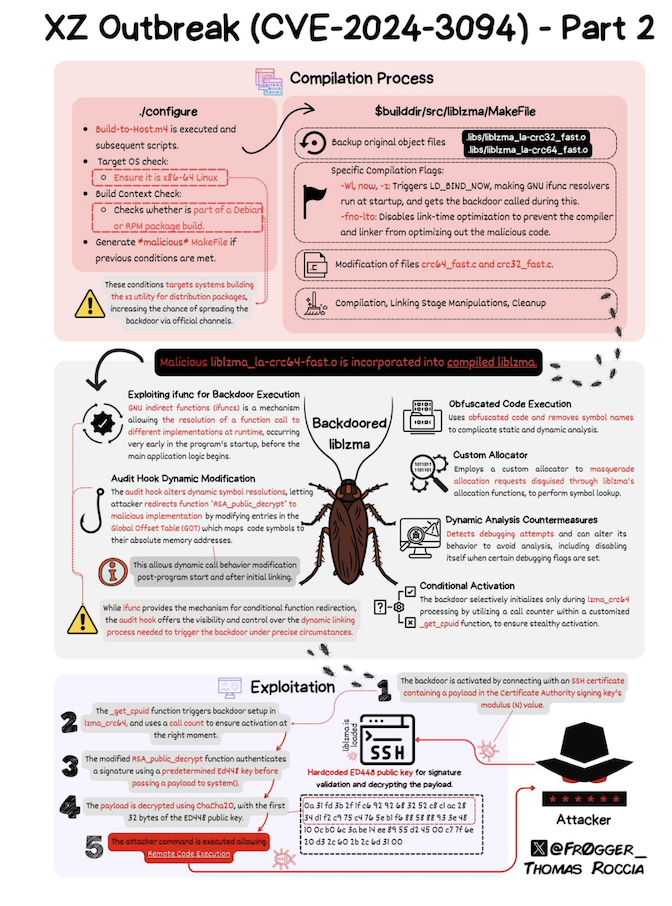
CVE-2024-3094 represents a significant security risk, stemming from malicious code discovered within the source files of xz, starting from version 5.6.0. The intricate process of building liblzma extracts a precompiled object file from a disguised test file within the source code. This file is then utilized to alter specific functions within the liblzma code, resulting in a modified liblzma library that can be utilized by any software linked to it. This manipulation opens doors for intercepting and modifying data interaction with said library.
The Severity and Impact – CVSS Score of 10.0
With a CVSS score of 10.0 (CRITICAL), CVE-2024-3094 stands as a formidable threat, capable of inflicting substantial damage to security. Its severity cannot be overstated, as it poses a grave risk to affected systems. Given that SSH relies on liblzma, exploitation of this vulnerability could lead to unauthorized access, allowing attackers to execute arbitrary system commands with impunity.
The ramifications of CVE-2024-3094 extend far and wide, affecting a myriad of systems and applications reliant on liblzma. From various Linux distributions like Ubuntu, Debian, CentOS, to a plethora of software applications, the vulnerability casts a wide net of potential targets. Furthermore, servers utilizing SSH for secure connections are also susceptible, further compounding the risk landscape.
How to protect you from vulnerability CVE-2024-3094
In the face of such a critical vulnerability, proactive measures are imperative to safeguard systems and data. Organizations must heed the following recommendations to mitigate the risk posed by CVE-2024-3094:
- Update XZ Utils: Ensure that your XZ Utils version is not susceptible to the vulnerability. Check for updates regularly and apply them promptly to fortify your system against potential exploits.
- Patch or Replace liblzma: For systems reliant on liblzma, seek out available updates or patches to rectify the vulnerability. In cases where immediate updates are unattainable, consider replacing liblzma with an unaffected version as a stop-gap measure.
- Stay Informed: Keep abreast of security updates and alerts pertaining to XZ Utils and liblzma. Subscribe to security bulletins from your Linux distribution or follow official security accounts on social media platforms.
- Conduct Regular Audits: Perform routine security audits on your systems to detect any anomalous activities or exploitation attempts. Scrutinize access logs, SSH connections, and other indicators of compromise diligently.
- Restrict SSH Access: Limit SSH access exclusively to authorized users and consider implementing public key authentication for enhanced security.
- Consider Alternatives: If immediate updates or patches are unfeasible, contemplate temporarily disabling the use of XZ Utils or liblzma until appropriate measures can be implemented.
Verifying and Securing your system
To ascertain whether your system is vulnerable to CVE-2024-3094, follow these steps:
- Check XZ Utils Version: Verify the installed version of XZ Utils on your system using the command “xz –version.” If your version predates 5.6.0, you may be safe, but always ensure to verify for any available updates.
- Refer to Security Alerts: Refer to security bulletins from your Linux distribution or software provider for specific information regarding CVE-2024-3094. If updates or patches are available, adhere to the provided instructions for implementation.
- Audit Your Systems: Scrutinize system logs for any suspicious activities or signs of exploitation related to XZ Utils or liblzma.
- Check Application Dependencies: Identify applications or services reliant on liblzma and verify if they are employing a vulnerable version. Consult official sources for guidance on safeguarding such applications.
More information about how works this vulnerability. The following infographic is created by Thomas Roccia.