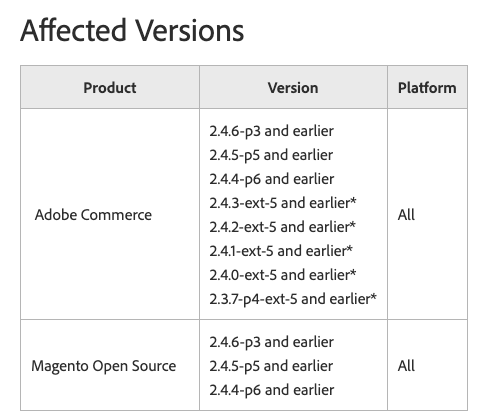
CVE-2024-20720 is affecting various versions of Adobe Commerce. Understanding this vulnerability and taking proactive measures is crucial to ensure the security of your online presence.
The CVE-2024-20720 affects versions of Adobe Commerce 2.4.6-p3, 2.4.5-p5, 2.4.4-p6, and earlier. It is an OS Command Injection vulnerability that could lead to arbitrary code execution by an attacker.
Here are the details:
- Vulnerability Impact:
- Arbitrary Code Execution: Yes.
- Requires Administrator Privileges: Yes.
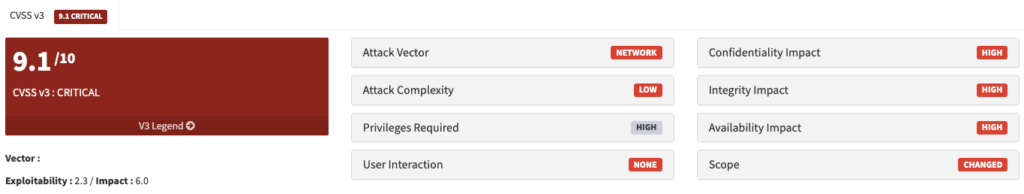
- CVSS Base Score: 9.1 (Critical).
- Description: This vulnerability allows an attacker to execute arbitrary code through command injection in the operating system.
- Uncontrolled Resource Consumption:
- Application Denial of Service: Yes.
- Requires Administrator Privileges: Yes.
- CVSS Base Score: 5.7 (Important).
- Description: This vulnerability can cause a denial of service in the application.
If you are using Adobe Commerce in any of the affected versions, it is recommended to update to the patched versions to mitigate these security risks
How to protect your website against CVE-2024-20720
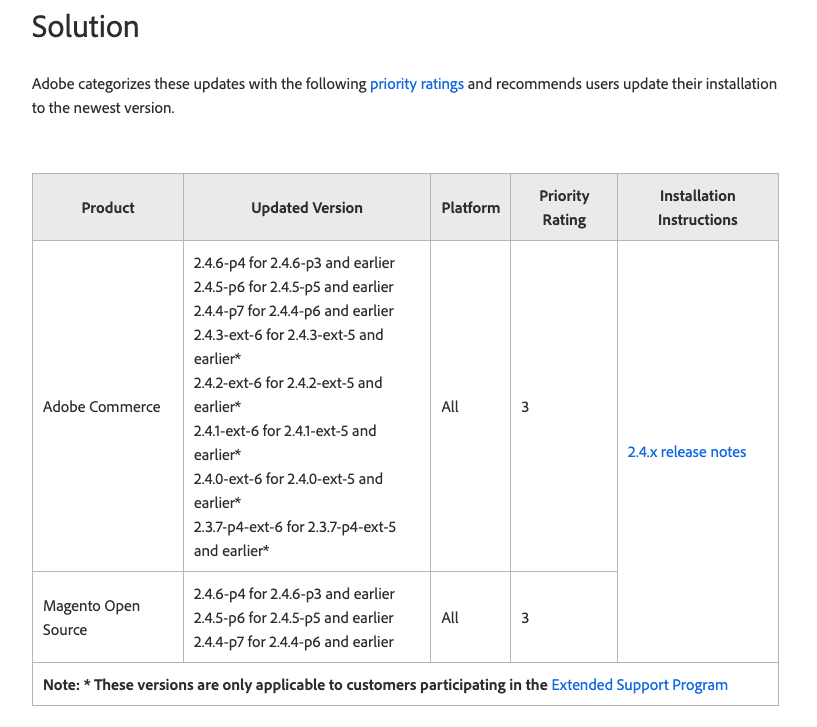
Ensure that you are using a patched version of Adobe Commerce. Update to 2.4.6-p4, 2.4.5-p6, or later versions, which contain fixes for this vulnerability.
To protect your website from the CVE-2024-20720 vulnerability, follow these recommendations:
- Update Adobe Commerce:
- Ensure that you are using a patched version of Adobe Commerce. Update to 2.4.6-p4, 2.4.5-p6, or later versions, which contain fixes for this vulnerability.
- Ensure that you are using a patched version of Adobe Commerce. Update to 2.4.6-p4, 2.4.5-p6, or later versions, which contain fixes for this vulnerability.
- Code Audit:
- Conduct a code audit to search for potential command injections. Verify that there are no unvalidated user inputs that could be exploited.
- Conduct a code audit to search for potential command injections. Verify that there are no unvalidated user inputs that could be exploited.
- User Input Validation:
- Implement strict validation of user inputs. Properly filter and escape data before executing commands in the operating system.
- Implement strict validation of user inputs. Properly filter and escape data before executing commands in the operating system.
- Principle of Least Privilege:
- Limit user and service privileges in your application. Only grant administrator access when absolutely necessary.
- Limit user and service privileges in your application. Only grant administrator access when absolutely necessary.
- Firewall and Access Rules:
- Configure firewall rules to restrict access to sensitive services. Allow connections only from trusted IP addresses.
- Configure firewall rules to restrict access to sensitive services. Allow connections only from trusted IP addresses.
- Monitoring and Logging:
- Establish active monitoring of application and system logs. Look for signs of suspicious activity or attempted command injections.
- Establish active monitoring of application and system logs. Look for signs of suspicious activity or attempted command injections.
- Layered Security:
- Implement security measures in layers. This includes firewalls, intrusion detection systems (IDS), and web application security solutions (WAF).
How to patch the vulnerability
To apply the necessary patches and protect your website from the CVE-2024-20720 vulnerability, follow these steps:
- Check the Current Version:
- Make sure you know which version of Adobe Commerce you are currently using. This is crucial for applying the correct patches.
- Make sure you know which version of Adobe Commerce you are currently using. This is crucial for applying the correct patches.
- Download the Patches:
- Visit the official Adobe Commerce website or support portal to find specific patches for your affected version. Download the corresponding patch files.
- Visit the official Adobe Commerce website or support portal to find specific patches for your affected version. Download the corresponding patch files.
- Back Up Your Site:
- Before applying any patches, perform a full backup of your website. This ensures that you can restore your site in case of issues.
- Before applying any patches, perform a full backup of your website. This ensures that you can restore your site in case of issues.
- Apply the Patches:
- Follow the instructions provided by Adobe Commerce to apply the patches. This may involve replacing specific files or running update scripts.
- Follow the instructions provided by Adobe Commerce to apply the patches. This may involve replacing specific files or running update scripts.
- Verify the Installation:
- After applying the patches, verify that the installation was successful. Check that the Adobe Commerce version is now updated and does not exhibit the vulnerability.
- After applying the patches, verify that the installation was successful. Check that the Adobe Commerce version is now updated and does not exhibit the vulnerability.
- Functional Testing:
- Conduct thorough testing on your website to ensure that all functions continue to work correctly after applying the patches.
- Conduct thorough testing on your website to ensure that all functions continue to work correctly after applying the patches.
- Ongoing Monitoring:
- Set up continuous monitoring to detect any issues or unusual behavior after patch application. This will help you identify any problems early.
- Set up continuous monitoring to detect any issues or unusual behavior after patch application. This will help you identify any problems early.
- User Communication:
- If your website has users or clients, inform them that patches have been applied and their security is protected.
How to know if your website is affected by the CVE-2024-20720
To verify if your website is affected by the CVE-2024-20720 vulnerability, follow these steps:
- Check Adobe Commerce Version:
- Verify the version of Adobe Commerce you are currently using. You can find this information in the documentation or your website’s configuration.
- Verify the version of Adobe Commerce you are currently using. You can find this information in the documentation or your website’s configuration.
- Review Release Notes:
- Examine Adobe Commerce release notes to determine if your specific version is affected by this vulnerability. Look for any mention of CVE-2024-20720 or related issues.
- Examine Adobe Commerce release notes to determine if your specific version is affected by this vulnerability. Look for any mention of CVE-2024-20720 or related issues.
- Run Security Scans:
- Use security scanning tools to search for known vulnerabilities on your website. These tools can identify whether your site is using a vulnerable version of Adobe Commerce.
- Use security scanning tools to search for known vulnerabilities on your website. These tools can identify whether your site is using a vulnerable version of Adobe Commerce.
- Manual Code Audit:
- Inspect your website’s code for potential command injections. Pay special attention to areas where user inputs are processed or commands are executed in the operating system.
- Inspect your website’s code for potential command injections. Pay special attention to areas where user inputs are processed or commands are executed in the operating system.
- Proof of Concept (PoC):
- If you have access to a test environment, attempt to reproduce the vulnerability using a proof of concept (PoC). This will help confirm if your website is vulnerable.


