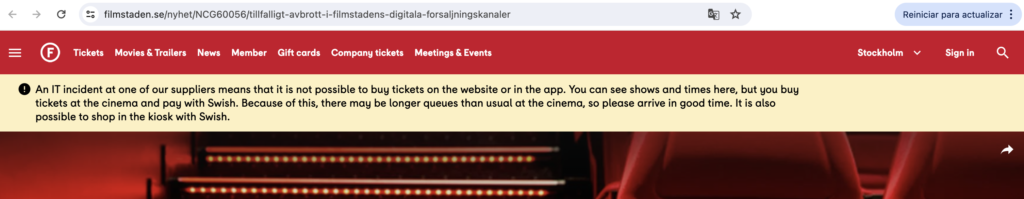
The Akira ransomware attack on Tietoevry was a cybersecurity incident that impacted several clients of the Finnish software and IT services company in Sweden. The attack occurred on the night of January 19-20, 2024, causing disruptions to healthcare systems, local governments, retail businesses, and the country’s largest cinema chain.
Tietoevry reported that they isolated the compromised infrastructure and were actively working to restore services as quickly as possible. However, they cautioned that the recovery process might extend over several days or even weeks, depending on the nature of the incident and the specific systems of each client.
Impact of the ransomware attack at Tietoevry
Numerous organizations, including government authorities, universities, and colleges relying on Tietoevry’s Primula human resources and payroll management system, were among those affected. Issues were also reported in the medical records system of patients in the Uppsala region, along with some financial systems.
The ransomware attack on Tietoevry was attributed to the cybercriminal group Akira, known for extorting large corporations and organizations. The demanded ransom amount remains undisclosed, and it’s unclear whether Tietoevry acquiesced to pay it.
Who is Akira?
The cybercriminal group Akira is a hacking gang specializing in extorting large corporations and organizations through ransomware attacks. Ransomware is a type of malware that encrypts victims’ files and devices, demanding a ransom for their recovery. Akira employs a double extortion method, stealing critical data before encryption and threatening to publish it unless the ransom is paid.
Emerging in March 2023, Akira is believed to be linked to the Conti group, itself a descendant of the Ryuk ransomware. Akira operates as a Ransomware-as-a-Service (RaaS), providing its malicious software to other cybercriminals in exchange for a share of the ransom. While primarily targeting U.S. and Canadian companies, Akira has also attacked organizations in Europe, such as the IT systems in South Westphalia, Germany.
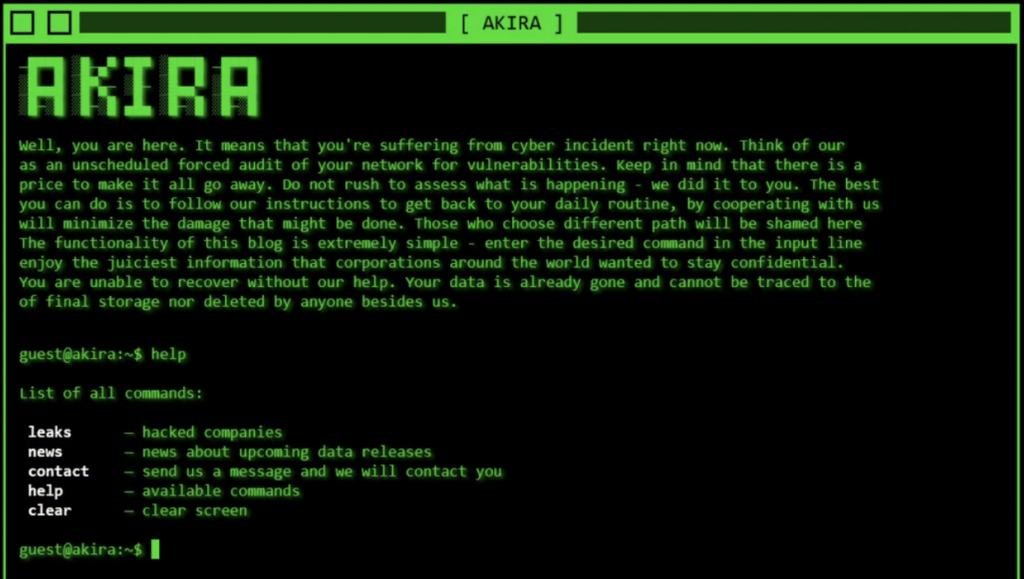
Akira maintains a website on the Tor network, where stolen data and ransom demands are published. The site features a retro design reminiscent of 1980s green-screen consoles. Reports suggest that Akira gives victims the option to pay for file decryption or data deletion, an unusual practice in the ransomware landscape.
As one of the most active and dangerous ransomware families today, Akira poses a serious threat to the cybersecurity of businesses and organizations. To defend against such attacks, it is recommended to have updated backups, use antivirus software, avoid opening suspicious emails or files, and educate staff on cybersecurity best practices.
For more information about the cybercriminal group and how Akira Ransomware group works.


