Check Point is warning of a zero-day vulnerability (CVE-2024-24919) in its Network Security gateway products that threat actors have exploited in the wild.
CVE-2024-24919
CVE-2024-24919 is a vulnerability affecting Check Point security gateways. Once these gateways are connected to the Internet and enabled with Remote Access VPN or Mobile Access software blades, an attacker potentially can read certain information. The severity rating for this vulnerability is high, with a CVSS score of 7.5.
The main target of attackers has been old local accounts using password-only authentication. However, Check Point strongly recommends not using this authentication method.
To address this vulnerability, a security solution has been provided to mitigate the issue. If you are a Check Point user, ensure to apply this patch to protect your VPN remote access networks from information disclosure.
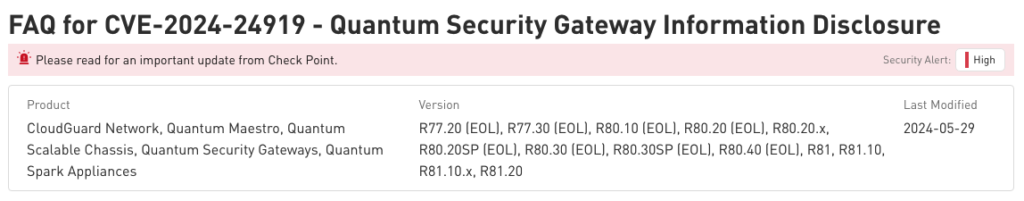
Hotfixes availables
The hotfixes for CVE-2024-24919 vulnerability are available in the following versions of Check Point Security Gateway:
- R80.40 Jumbo Hotfix Accumulator (Take 142) or later.
- R81.20 Jumbo Hotfix Accumulator (Take 112) or later.
CVE-2024-24919 – Mitigation
To apply the hotfix to your specific version of Check Point Security Gateway, follow these steps:
- Verify your current version: Before applying any hotfix, make sure you know which version of Check Point you are using. You can check this in the management interface or through commands on the command line.
- Download the corresponding hotfix: Visit the official Check Point website and look for the specific hotfix for your version. Download it to an accessible location on your system.
- Perform a backup: Before making any changes, perform a full backup of your configuration. This will allow you to restore your system in case of any issues.
- Apply the hotfix:
– If you are using version R80.40, run the command to apply the hotfix:
# cd /path/to/hotfix
# ./UnixInstallScript
– If you are using version R81.20, run the command:
# cd /path/to/hotfix
# ./UnixInstallScript - Verify the installation: After applying the hotfix, verify that everything is functioning correctly. Conduct thorough testing to ensure there are no issues.
Always remember to follow the specific instructions provided by Check Point for your particular version.
Vulnerable versions
The vulnerable versions to CVE-2024-24919 in Check Point Security Gateway are as follows:
For Check Point Quantum Gateway and CloudGuard Network:
- Versions R81.20, R81.10, R81, R80.40.
For Check Point Spark:
- Versions R81.10, R80.2012.
Verify your current version
To verify the current version of Check Point Security Gateway, follow these steps:
- Access the administration interface of your Check Point Security Gateway. This is typically done through a secure connection via SSH or a web interface.
- On the command line, run the following command to retrieve information about the version:
#fw ver
This will display details such as the version, hotfix accumulator, and other relevant information. - Check the output of the command to find the specific version of Check Point you are using. For example, if you see something like “R81.20 Take 631”, that indicates you are using version R81.20 with hotfix accumulator Take 631.
- Remember that it’s always recommended to stay up-to-date with the latest versions to benefit from functional improvements, stability fixes, security enhancements, and protection against new and evolving attacks.


