CVE-2024-4577 is a critical argument injection vulnerability in PHP that can be exploited to achieve remote code execution (RCE). According to researchers from DEVCORE, this flaw stems from character encoding conversion errors, specifically affecting the “Best Fit” function in Windows. Here are the key details:
Description: The vulnerability allows unauthenticated attackers to gain complete control of affected PHP servers.
Origin: The issue arises from the omission of the “Best Fit” encoding conversion function in the Windows operating system during PHP implementation.
Impact: Attackers can bypass protections from CVE-2012-1823 and execute arbitrary code on remote PHP servers.
Risk Scenarios:
- CGI Mode: If PHP is running in CGI mode, the server might be at risk.
- PHP Binary Exposure: If the PHP binary is accessible in a web directory, it could affect systems on the Internet.
Relation to CVE-2012-1823: CVE-2024-4577 bypasses the patch for CVE-2012-1823.
Proof of Concept: Researchers have published a PoC for this vulnerability.
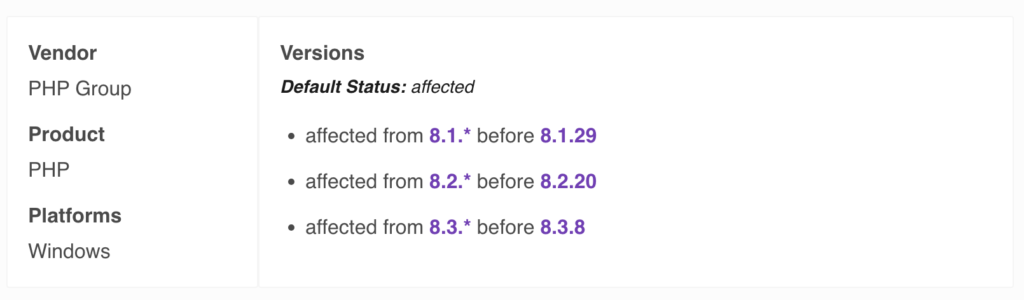
Affected versions
Patch for the vulnerability CVE-2024-4577
Today, there is no official patch available specifically for CVE-2024-4577. However, here are some mitigation recommendations:
- Software Update: Keep your PHP installation updated. Although there is no specific patch, general updates can help protect against known vulnerabilities.
- Restrict Unnecessary Access: Limit access to your server to only what is essential. This reduces the attack surface.
- Monitor for Anomalies: Stay alert for any unusual activity on your server. Constant monitoring can help detect potential attacks.
Remember that CVE-2024-4577 is a bypass of the patch for CVE-2012-1823. Always stay alert and follow best security practices. If you have any questions, feel free to ask.
Protecting your PHP server
To protect your PHP server, here are some security recommendations:
Update PHP: Use the latest stable version of PHP to fix known vulnerabilities.
Set up proper permissions: Ensure that files and directories have limited permissions. Prevent the execution of dangerous functions.
Validate and filter input data: Escape and filter any information sent by users to prevent attacks such as SQL injection.
Use HTTPS: All communication between the client and server should be via HTTPS.
Hide PHP: Avoid placing PHP code in the root directory of the server. Use a folder structure that prevents direct access to the files.


