In this CTF, we invite you to unravel the mysteries of hashing, a fundamental concept in the world of cybersecurity. As you navigate through a series of thought-provoking challenges, you’ll delve into the art and science of creating and deciphering cryptographic hash functions.
MD5 Hashing
One use for hashes is a data structure called a hash table, widely used in computer software for rapid data lookup. Hash functions accelerate table or database lookup by detecting duplicated records in a large file. An example of this is finding similar stretches in DNA sequences.
They are also useful in cryptography; the MD5 algorithm is a common hash function producing a 128-bit hash value. Although MD5 was initially designed to be used as a cryptographic hash function, it has been found to suffer from extensive vulnerabilities. It can still be used as a checksum to verify data integrity, but only against unintentional corruption.
SHA-1 Hashing
SHA-1 produces a 160-bit (20-byte) hash value known as a message digest. A SHA-1 hash value is typically rendered as a 40-digit, hexadecimal number.
Files are subjected to hashing algorithms to generate a checksum. A checksum is a small-sized datum derived from a block of digital data for the purpose of detecting errors that may have been introduced during its transmission or storage. It is usually applied to an installation file after it is received from the download server. By themselves, checksums are often used to verify data integrity but they are not relied upon to verify data authenticity.
1-What is the MD5 hash for the string ‘CyberGuardianHub’?
2-What is the SHA-1 hash for the string ‘CyberGuardianHub’?
3-Using the following picture, What is the MD5 and SHA-1 hash?

Image to hash
Note: Use CyberChef to hash or command tools.
More information about Hashing and CyberChef:
CTF 3 – Modern encryption: Hashing – Answers
Results
Try again!!
#1. What is the MD5 hash for the string 'CyberGuardianHub'?
#2. What is the SHA-1 hash for the string 'CyberGuardianHub'?
#3. Using the picture, What is the MD5?
#4. Using the picture, What is the SHA-1?
CTF 2 – Enigma Machine: Decrypt the message – Solutions
1. The ‘Encrypted Message’ is: LXPWL EJXHO RDAVA ZTCGG FFLIA SHTNH HUDLW KPBFZ PAIFO ZRXKE TLCFL GZLYX ZRIQZ XVHCC ZGN. What is the ouput returned?
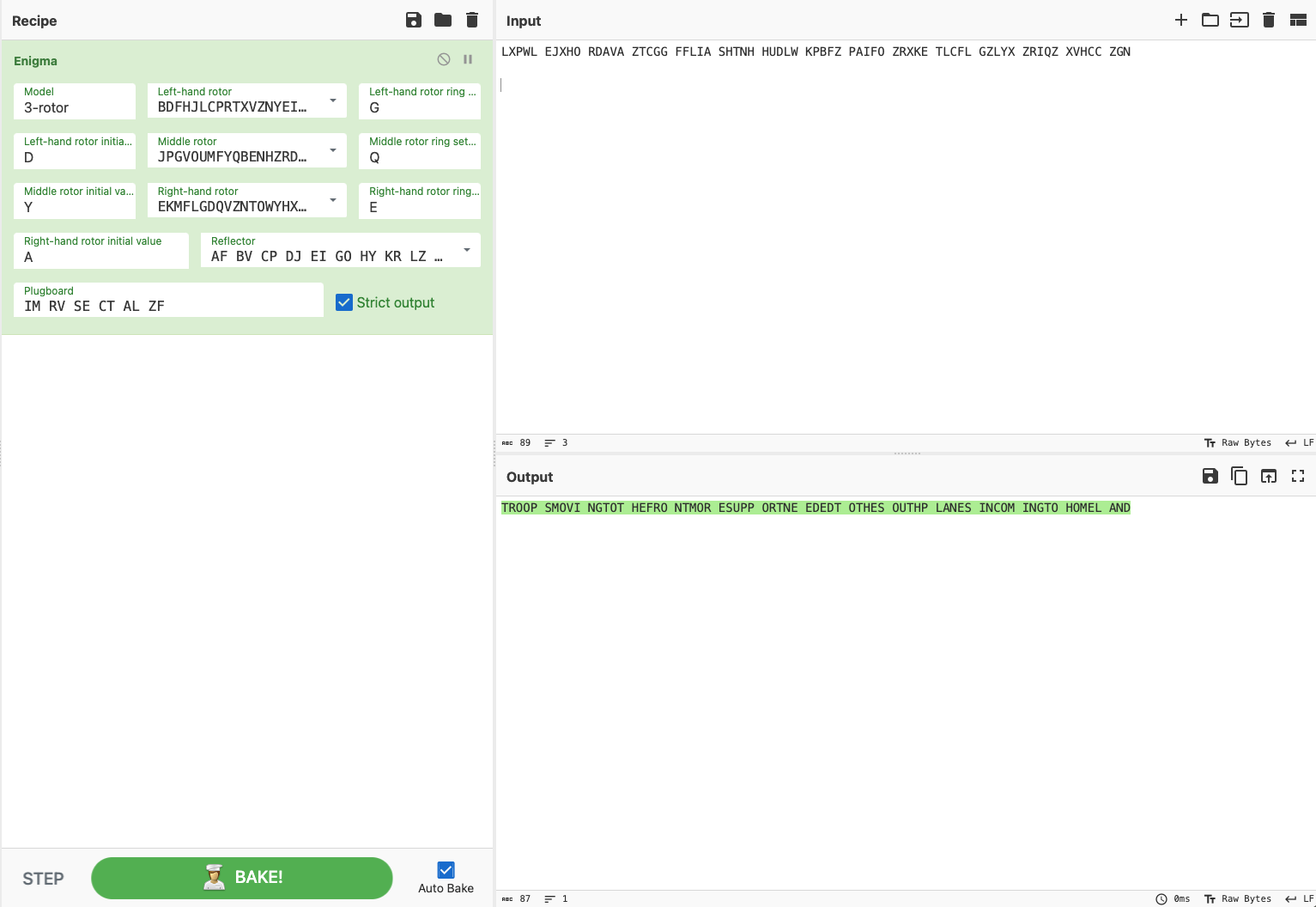
TROOP SMOVI NGTOT HEFRO NTMOR ESUPP ORTNE EDEDT OTHES OUTHP LANES INCOM INGTO HOMEL AND


