Recently, a critical vulnerability, CVE-2023-45590, has emerged, impacting Fortinet FortiClientLinux. Let’s delve into the details and explore how to mitigate this threat effectively.
CVE-2023-45590 – Details
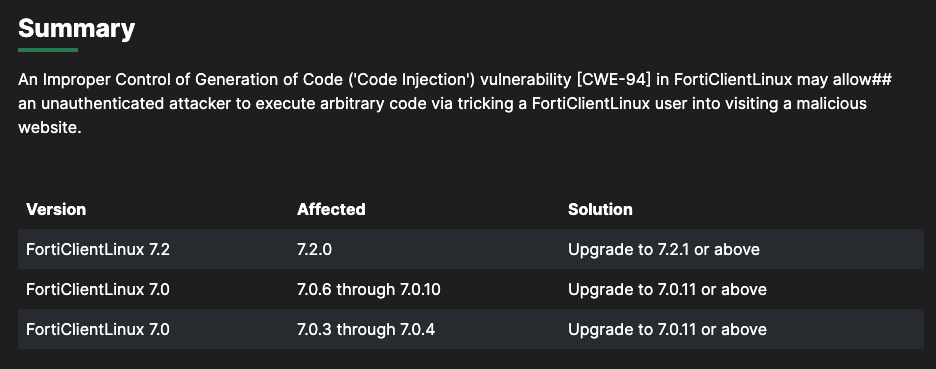
CVE-2023-45590 is a vulnerability concerning code injection (inadequate control of code generation) found in Fortinet FortiClientLinux versions 7.2.0, 7.0.6 to 7.0.10, and 7.0.3 to 7.0.4.
Exploiting this flaw could enable attackers to execute unauthorized code or commands by deceiving FortiClientLinux users into visiting malicious websites.
Key Points:
- Description: Code injection vulnerability in Fortinet FortiClientLinux.
- Impact: Allows unauthorized code execution by luring users to malicious sites.
- Severity: Rated critical with a CVSS score of 9.4.
For further insights, refer to the FortiGuard reference link.
CVE-2023-45590 -Mitigation
Patch Available
The good news is that patches are available to address CVE-2023-45590 in Fortinet FortiClientLinux. The vulnerability has been tackled with the release of versions 7.2.1 and 7.0.11 of FortiClientLinux. Therefore, it’s highly advisable to upgrade to these versions promptly to shield your systems.
Steps to Apply Patches:
- Verify Current Version: Before applying patches, ascertain your FortiClientLinux version.
- Download Patches: Access the official Fortinet website or support portal to acquire the latest patches.
- Backup Your System: Prioritize a complete system backup to mitigate risks during the update process.
- Install Patches: Download and install the appropriate patches following Fortinet’s instructions.
- Verify Installation: Confirm successful patch installation by checking the updated FortiClientLinux version.
- Reboot Your System: Ensure changes take effect by rebooting your system.
- Monitor and Evaluate: Post-patching, monitor system performance to ensure effectiveness and vulnerability resolution.
How to check if your FortiClientLinux is vulnerable
To check the current FortiClientLinux version on your system:
- Open Terminal or Command Line: Launch the terminal or command line interface on your system.
- Execute Version Command: Type the command
forticlient --versionand press Enter. - Review Output: The terminal will display the current FortiClientLinux version in the appropriate format (e.g., “FortiClientLinux version: 7.2.1”).
By adhering to these steps and staying proactive in applying patches, you can fortify your systems against CVE-2023-45590 and other potential threats.


