CVE-2024-1086 is a critical vulnerability affecting Linux operating systems. It allows local users to execute code with elevated privileges, potentially granting them control over the entire system. The vulnerability lies within the netfilter component: nf_tables of the Linux kernel and can be exploited to achieve local privilege escalation. It is recommended to update to the kernel version that includes the fix (commit f342de4e2f33e0e39165d8639387aa6c19dff660).
Protecting your system against CVE-2024-1086
To protect your system against CVE-2024-1086, follow these steps:
Update your kernel: Ensure you are using a version of the Linux kernel that includes the fix for this vulnerability. You can check the current version of your kernel with the following command in the terminal:
uname -r
If you are not using the corrected version, update your system. In most distributions, you can do this with:
sudo apt update sudo apt upgrade
Restart your system: After updating the kernel, restart your system to apply the changes.
Monitor security updates: Stay informed about security updates for your distribution. Subscribe to mailing lists or follow official accounts on social media to receive notifications about patches and updates.
Configure a firewall: Set up a firewall to limit access to non-essential ports and services. This will help protect your system against external attacks.
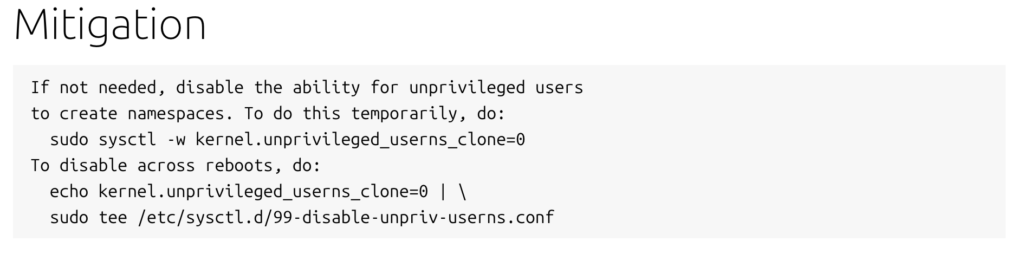
Limit user privileges: Avoid running applications with administrator or root privileges unless absolutely necessary. Use standard user accounts for daily tasks.
Remember, security is an ongoing process. Keep your system up to date.
Kernels afected
The vulnerability CVE-2024-1086 affects the netfilter component: nf_tables of the Linux kernel and allows local privilege escalation. Here are the affected kernel versions:
- Bionic (18.04): Available in version 4.15.0-223.235.
- Focal (20.04): Available in version 5.4.0-174.193.
- Jammy (22.04): Available in version 5.15.0-101.111.
- Mantic (22.10): Available in version 6.5.0-26.26.
- Noble (23.04): Pending release in version 6.8.0-7.7.
- Trusty (14.04): Not vulnerable (version 3.11.0-12.19).
Upstream:
- Available in version 6.8~rc2.
Linux AWS:
- Bionic (18.04): Available in version 4.15.0-1166.179.
- Focal (20.04): Available in version 5.4.0-1121.131.
- Jammy (22.04): Available in version 5.15.0-1056.61.
- Mantic (22.10): Available in version 6.5.0-1016.16.
- Noble (23.04): Pending release in version 4.4.0-1129.135.
Upstream:
- Available in version 6.8~rc2.
Linux AWS 5.0:
- Bionic (18.04): Ignored (replaced by linux-aws-5.3).
Linux AWS 5.11:
- Bionic (18.04): Does not exist (replaced by linux-aws-5.13).
In summary, if you are using an affected kernel version, I recommend updating to the corrected version (commit f342de4e2f33e0e39165d8639387aa6c19dff660).


