CVE-2024-32896 is a privilege escalation vulnerability affecting Android devices, specifically Pixel devices. This vulnerability is due to a logical error in the code, which allows a local attacker to escalate their privileges without requiring additional permissions. Exploiting this vulnerability requires user interaction.
CVE-2024-32896 Vulnerability
This vulnerability has been actively exploited in targeted attacks, although the details of these attacks and the threat actors involved have not been fully disclosed by Google. It was first highlighted in Google’s June 2024 security bulletin, which noted that CVE-2024-32896 was one of several high-severity vulnerabilities patched in that release. Google strongly recommends that all Pixel users apply the latest updates immediately to protect their devices from potential attacks
Technical Details:
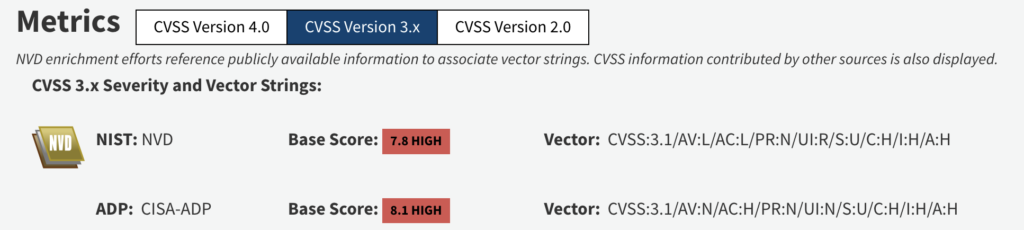
- Vulnerability Type: Privilege escalation.
- Attack Vector: Local (requires physical access to the device).
- User Interaction: Required.
- Impact: High, as it can compromise the confidentiality, integrity, and availability of the affected system.
How can I check if my system is affected?
To check if the vulnerability affects your device, follow these steps:
1. Verify the Security Version:
- Go to Settings on your device.
- Scroll down and select About phone or About device.
- Look for the Android Version and Security Patch Level.
- If the Security Patch Level is later than June 2024, your device should be protected against this vulnerability.
CVE-2024-32896 Mitigation
To mitigate the risks associated with CVE-2024-32896, follow these steps:
- Update Your Device:
- Go to Settings > System > System Update.
- Download and install any available updates. Ensure that your device has the June 2024 security patch or later.
- Review the Google Security Bulletin: Check the June 2024 Security Bulletin to confirm that it includes the fix for CVE-2024-32896.
- Enable Automatic Updates: To keep your device protected, go to Settings > System > System Update > Advanced options, and turn on Automatic updates.


