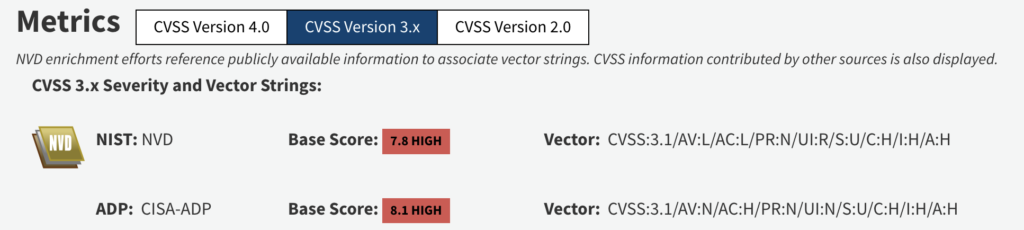
The CVE-2024-45622 vulnerability affects ASIS (also known as Aplikasi Sistem Sekolah using CodeIgniter 3) in versions 3.0.0 to 3.2.0. This vulnerability allows attackers to inject SQL through the index.php file and exploit it to bypass authentication.
Check if your system is affected
To check if your application is vulnerable to CVE-2024-45622, you can follow these steps:
- Check the CodeIgniter Version: Verify if you’re using one of the affected versions (3.0.0 to 3.2.0). If so, your application is likely vulnerable.
- Analyze the Code: Review the index.php file and other entry points in your application for potential SQL injection vulnerabilities. Look for code patterns that do not properly validate or sanitize user input.
- Vulnerability Scanning: Use vulnerability scanning tools such as OWASP ZAP or Burp Suite to analyze your application for SQL injections and other vulnerabilities.
- Review Server Logs: Check your web server and database logs for signs of SQL injection attempts. Unusual patterns or errors related to SQL queries may indicate exploitation attempts.
- Penetration Testing: Perform penetration testing specifically targeting this vulnerability. Try injecting SQL code into your application’s entry points to see if you can bypass authentication or access unauthorized data.
If you find signs of vulnerability, it’s crucial to take immediate action to mitigate the risk, such as updating CodeIgniter and applying temporary patches.
CVE-2024-45622 Mitigation
To protect your application from the CVE-2024-45622 vulnerability, you can follow these steps:
- Update CodeIgniter: Ensure you update to the latest version of CodeIgniter that has patched this vulnerability. Check the official CodeIgniter documentation for the most recent version.
- Input Validation: Implement strict validation for all user inputs. Use escaping and sanitization functions to prevent SQL injection.
- Use an ORM: Consider using an ORM (Object-Relational Mapping) such as Eloquent, which comes with Laravel, to handle database queries securely.
- Temporary Patch: If you cannot update immediately, apply a temporary patch that filters and validates inputs in the index.php file to prevent SQL injections.
- Monitoring and Auditing: Implement monitoring and auditing tools to quickly detect and respond to any exploitation attempts.
- Review Configurations: Ensure that your server and database configurations are optimized for security, such as disabling unnecessary functions and restricting permissions.
Review your server logs for SQL injection patterns and perform penetration testing focused on this vulnerability to check if it affects your system.


