What is Zero Trust?
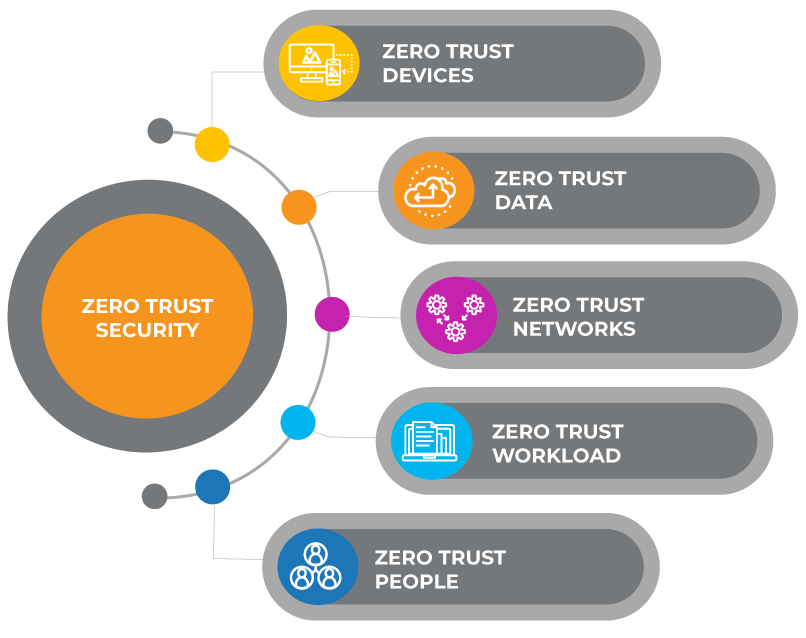
Zero Trust is a security model that protects the data, users, and devices of an organization from threats in a continuous and adaptive way. It is based on the principle of never trust and always verify every connection, device, and transaction. Some of the benefits of Zero Trust are:
- It enables a secure hybrid workforce by applying security policies that adapt to the context of each user and device.
- It protects the most critical resources by limiting the access and encrypting the data, even when it moves outside the network.
- Reduce the security vulnerabilities by providing visibility, risk-based access controls, and automated policies.
- It minimizes the impact of malicious actors by using a layered defense that explicitly verifies all access requests.
- It stays ahead of the compliance requirements by using a comprehensive strategy that helps protect, manage, and govern the data seamlessly.
The importance to embrace Security Evolution with Zero Trust this 2024
Security Evolution with Zero Trust is a concept that refers to the need for organizations to adopt a more proactive and adaptive approach to cybersecurity, especially in the face of the increasing and evolving threats in the digital age. Zero Trust is a security model that protects the data, users, and devices of an organization from threats in a continuous and adaptive way. It is based on the principle of never trust and always verify every connection, device, and transaction.
Some of the reasons why embracing Security Evolution with Zero Trust is important this 2024 are:
- The pandemic has accelerated the adoption of cloud and remote working technologies, which have increased the attack surface and complexity of the network.
- The regulatory standards and compliance requirements have become more stringent and diverse, requiring organizations to protect, manage, and govern their data seamlessly.
- The attackers have become more sophisticated and persistent, using emerging technologies such as AI and machine learning to create and launch more advanced and targeted attacks.
- The trust deficit has grown among customers, partners, and stakeholders, who demand more transparency and accountability from organizations regarding their cybersecurity practices.
How does Zero Trust Work?
Zero Trust is a security model that works by verifying the identity and permissions of every user and device that tries to access the network or application, regardless of where they are or what they are accessing. It also monitors and adapts to the changing context of each request, such as the location, device, frequency, or risk level. Zero Trust uses a layered defense that consists of several components, such as:
- Identity and access management (IAM), which authenticates and authorizes users and devices based on factors such as passwords, biometrics, tokens, or certificates.
- Microsegmentation, which divides the network into smaller zones or perimeters, each with its own security policies and controls.
- Data encryption, which protects the data at rest and in transit, even when it moves outside the network perimeter.
- Endpoint security, which secures the devices that connect to the network, such as laptops, smartphones, or IoT devices, by using antivirus, firewall, or patch management software.
- Network security, which monitors and analyzes the network traffic and blocks any malicious or suspicious activity, such as malware, phishing, or denial-of-service attacks.
Zero Trust is not a single product or technology, but rather a holistic approach that requires a shift in mindset and culture.
It is based on the principle of “never trust, always verify” and assumes that threats can come from anywhere, inside or outside the network.
By implementing Zero Trust, organizations can improve their security posture, reduce their attack surface, and comply with the regulatory standards.
Some Challenges implementing it!
Some of the challenges of implementing Zero Trust are:
- Complex infrastructure: Many organizations have a mix of legacy and new systems, on-premises and cloud environments, and multiple servers, proxies, databases, and applications. Securing each segment of the network and ensuring interoperability can be difficult.
- Cost and effort: Implementing Zero Trust requires time, human, and financial resources. It involves segmenting the network, verifying the identity and permissions of every user and device, and monitoring and adapting to the context of each request.
- Flexible software: Implementing Zero Trust may require using several tools, such as micro-segmentation, identity-aware proxies, and software-defined perimeter. Finding a flexible and integrated solution that can work with different environments and systems can be challenging.
These challenges can be overcome by using a holistic and strategic approach, collaborating with stakeholders, and choosing a reliable and scalable solution that meets the needs of the organization. Some examples are shown below.
Examples of Zero Trust
Zero Trust is a security model that requires verifying the identity and permissions of every user and device that tries to access the network or application, regardless of where they are or what they are accessing. Some examples of Zero Trust are:
- CrowdStrike is a cybersecurity company that provides a cloud-native platform for implementing Zero Trust. It uses advanced technologies such as risk-based multi-factor authentication, identity protection, next-generation endpoint security, and robust cloud workload technology to verify and protect users, devices, and data.
- Microsoft is a technology company that offers a comprehensive and integrated solution for Zero Trust. It uses Azure Active Directory, Microsoft Defender, Microsoft Cloud App Security, and Microsoft Endpoint Manager to provide identity and access management, endpoint security, network security, and data encryption for its customers and employees.
Best practices to implement it in your organization
Some of the best practices for implementing Zero Trust are:
Understand the protection surface: Identify and prioritize the assets, data, and resources that need to be protected, and map the connections and transactions between them.
Adopt policy-based controls: Define and enforce granular policies and rules that regulate the access and permissions of users and devices, based on factors such as identity, context, and risk.
Adopt multi-factor authentication: Use multiple methods of verifying the identity and trustworthiness of users and devices, such as passwords, biometrics, tokens, or certificates.
Take time selecting a vendor: Choose a reliable and scalable solution that can integrate with your existing infrastructure and systems, and provide comprehensive and flexible coverage across your network, data, and devices.
Play the long game: Implement Zero Trust as a continuous and adaptive process, not a one-time project, and monitor and update your policies and controls as your environment and threats evolve.
More information about this topic in the following sources: