Learn the Fundamentals of Cybersecurity: explore basic concepts, from data protection to common threats, to begin your journey in this essential field.
1. Confidentiality, Integrity, and Availability (CIA Triad)
The CIA Triad is the foundational model in cybersecurity and consists of three core principles: Confidentiality, Integrity, and Availability.
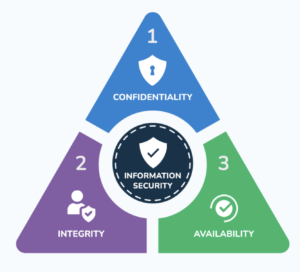
– Confidentiality: This principle focuses on ensuring that sensitive information is only accessible to authorized individuals. Techniques used to maintain confidentiality include encryption, access control mechanisms, and robust authentication methods. Confidentiality is critical to protect against unauthorized access to private information, especially in environments like financial institutions, healthcare, and government sectors. If breached, confidentiality violations can lead to data leaks, financial loss, and compromised personal information.
– Integrity: Integrity ensures that data remains accurate and unaltered unless modified by authorized personnel. It protects against unauthorized modifications or tampering. Integrity checks can be maintained through hashing algorithms like SHA-256, which detect even minor changes in data. For example, when sending a file or communication, hashing can confirm that the data hasn’t been altered during transmission, which is essential for maintaining trust in data systems.
– Availability: Availability ensures that authorized users can access necessary resources and data whenever required. Downtime or denial of access, whether due to system failure, cyberattacks (like DDoS attacks), or natural disasters, impacts availability. Redundancy, backup systems, and load balancing are key strategies to ensure high availability. This is especially crucial for online services, cloud applications, and financial systems where uptime is critical to business operations.
2. Types of Cyber Attacks
Understanding the most common types of cyberattacks is key to developing robust security measures:
– Phishing: One of the most common forms of social engineering, phishing involves sending deceptive emails or messages to trick users into divulging sensitive information such as passwords. These attacks often disguise themselves as legitimate requests from trusted entities. Phishing continues to evolve, with advanced techniques like spear phishing targeting specific individuals or organizations using personalized information.
– Malware: Malware refers to malicious software designed to harm, exploit, or otherwise compromise a system. Common types of malware include viruses, trojans, and spyware. Malware can be used to steal sensitive data, monitor user activity, or hijack systems for further attacks, such as launching DDoS attacks, etc.
– Ransomware: Ransomware is a type of malware that encrypts a victim’s files, making them inaccessible until a ransom is paid to the attacker. Recent attacks have targeted critical infrastructure, healthcare systems, and businesses, often demanding payments in cryptocurrency to unlock the encrypted data. Preventative measures include regular backups, patch management, and strong email filtering.
– DDoS (Distributed Denial of Service): A DDoS attack overwhelms a target’s system, server, or network by flooding it with massive amounts of traffic from multiple sources. This disrupts normal traffic, rendering the service unavailable to legitimate users. DDoS attacks can be particularly disruptive to online businesses and services that rely on uptime. Mitigation strategies involve using network traffic analysis tools, firewalls, and DDoS protection services to filter and manage incoming traffic.
– Insider Threats: Not all threats come from external attackers. Insider threats involve employees or contractors who intentionally or unintentionally compromise the organization’s security. These threats can stem from disgruntled employees leaking sensitive data, or from careless behavior, such as falling victim to phishing attacks. Mitigating insider threats requires robust access control, regular audits, and ongoing employee cybersecurity training.
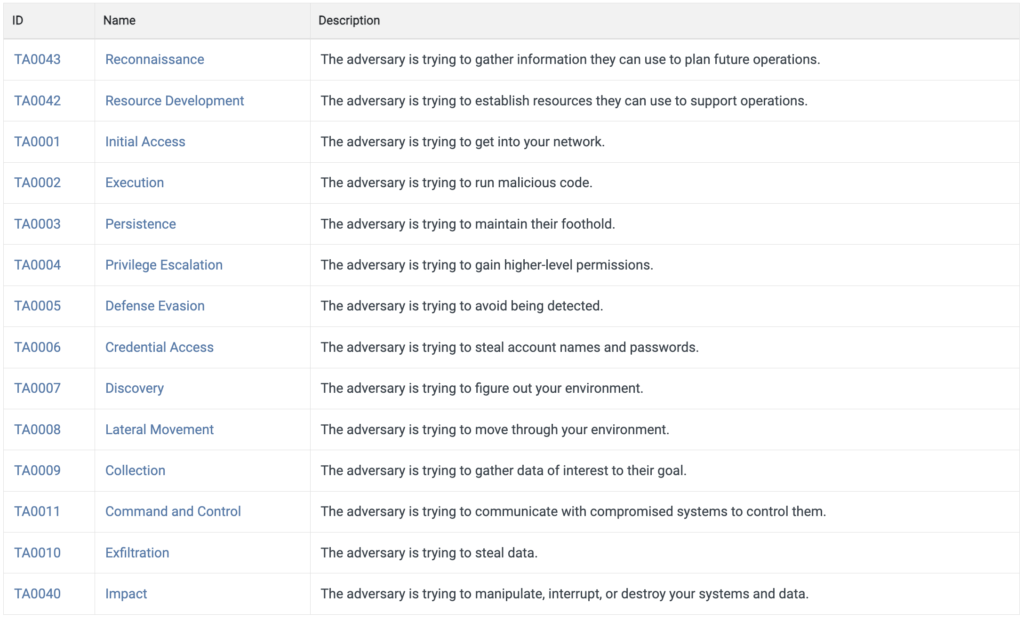
2.1 Mitre & Attack
For more information on this topic I suggest you visit the official Mitre Attack website. On this page you can see the techniques and tactics by which we rely on professionals in cybersecurity.
3. Authentication & Authorization
Authentication and authorization are two critical elements of access control in cybersecurity:
– Authentication: This process verifies the identity of a user attempting to access a system. Traditional authentication methods include usernames and passwords, but these can be vulnerable to attacks such as credential stuffing, brute force, or phishing. To strengthen security, more systems now use Multi-Factor Authentication (MFA). MFA requires users to provide two or more forms of authentication, like a password combined with a one-time code sent to their phone, or biometric verification such as fingerprint scanning. MFA significantly reduces the risk of unauthorized access, as attackers would need to compromise multiple authentication factors.
– Authorization: Once authenticated, authorization determines what resources the user can access and what actions they can perform. Role-Based Access Control (RBAC) is a common method of managing authorization. In RBAC, users are assigned roles based on their responsibilities, and each role has specific permissions. This minimizes the risk of granting excessive privileges, a principle known as “least privilege.” For example, an HR employee may have access to payroll data but not to company financial records. Authorization ensures that users only access information necessary for their role, reducing the potential impact of compromised accounts.
4. Encryption
Encryption is a method of converting data into a secure format that is unreadable without the appropriate decryption key. It plays a key role in protecting confidentiality and maintaining secure communication. There are two main types of encryption:
– Symmetric Encryption: In symmetric encryption, the system uses the same key for both encryption and decryption. This method efficiently encrypts large amounts of data and commonly secures data at rest, such as files on a hard drive or backups. However, the challenge with symmetric encryption lies in securely sharing the key with others. AES (Advanced Encryption Standard) is a widely used symmetric encryption algorithm, considered secure for many applications due to its strong encryption and speed.
– Asymmetric Encryption: Also known as public-key encryption, asymmetric encryption uses two different keys—a public key for encryption and a private key for decryption. This method ensures secure communications by allowing the public key to be shared openly, while only the corresponding private key decrypts the message. Asymmetric encryption protects secure online transactions, digital signatures, and SSL/TLS encryption in HTTPS connections. RSA (Rivest-Shamir-Adleman) remains one of the most widely used asymmetric encryption algorithms.
– SSL/TLS: Secure Sockets Layer (SSL) and its successor Transport Layer Security (TLS) are cryptographic protocols that provide secure communication over networks, such as the internet. SSL/TLS uses asymmetric encryption to establish a secure connection and symmetric encryption to exchange data. Websites using HTTPS rely on SSL/TLS to protect sensitive information, such as login credentials and payment details.
Encryption plays a crucial role in protecting sensitive data, whether during transit (e.g., emails, online banking) or at rest (e.g., stored files), and forms a fundamental part of many security protocols.


