GhostLocker Ransomware emerges as a menacing force, orchestrated by the notorious hacking group, GhostSec. We embark on a journey to decipher the intricacies of GhostLocker, understanding its evolution, tactics, and the imperative need for vigilance in the digital landscape.
The GhostSec Saga: Cybercrime Families
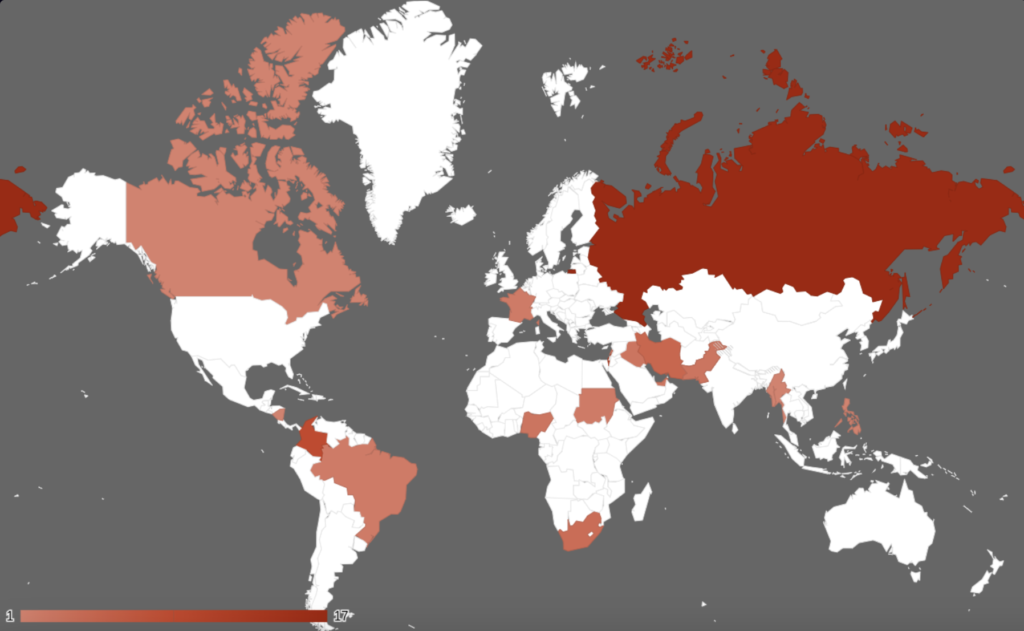
GhostSec, a formidable player in the cyber underworld, is a part of the modern league known as the “Five Families.” This league, including ThreatSec, Stormous, Blackforums, and SiegedSec, operates with diverse motives, contrasting Ghost Security Group’s counter-terrorism efforts. GhostSec, driven by financial gains, specializes in both single and double extortion attacks across global targets.
GhostLocker 2.0: A Glimpse into the Cryptic Future
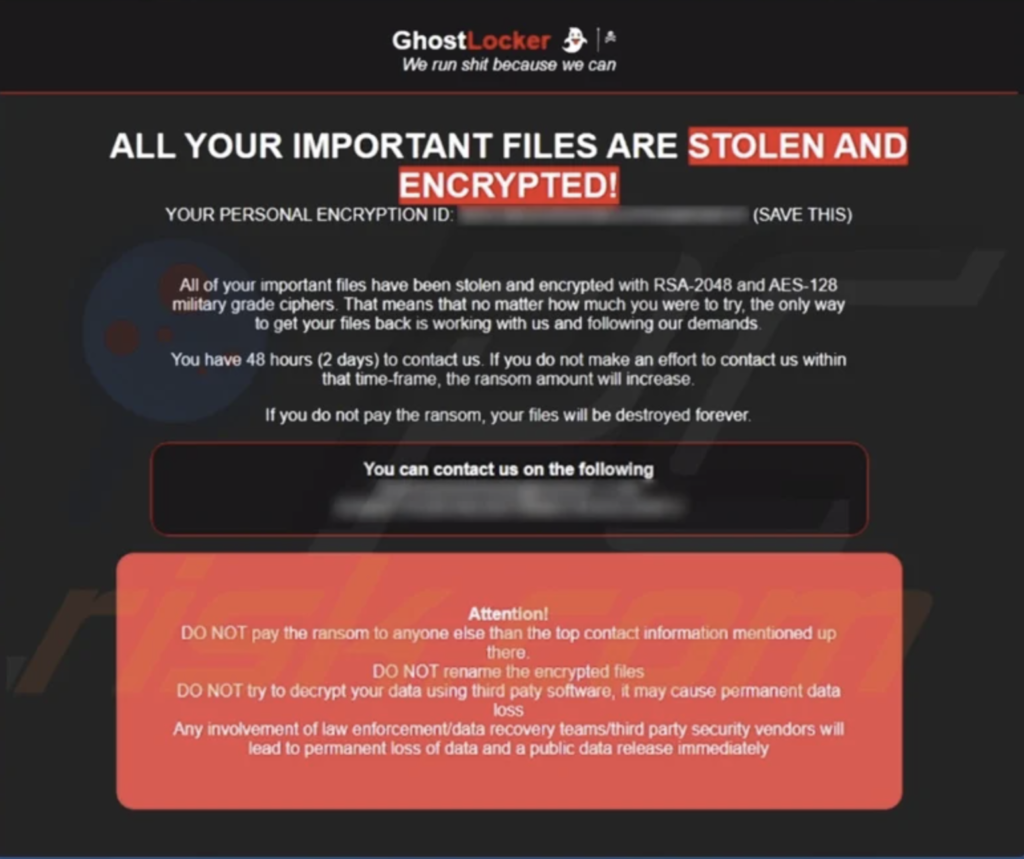
The latest evolution in GhostSec’s arsenal is the GhostLocker 2.0, a ransomware variant crafted in Golang. Employing RSA-2048 and AES-128 encryption algorithms, this variant boasts high-security standards. Files ensnared by GhostLocker bear the distinct “.ghost” extension, marking the aftermath of its encrypted conquests.
Collaborating with Stormous, GhostSec intensifies its impact through double extortion ransomware attacks spanning various industries and countries. Notably, they’ve birthed a Ransomware-as-a-Service (RaaS) initiative named STMX_GhostLocker, enticing affiliates with a menu of malicious possibilities.
Safeguarding against GhostLocker: Best Practices in Cybersecurity
Empower Your Defense: Proactive Measures Against GhostLocker Ransomware
In the ever-evolving landscape of cybersecurity, fortifying your digital stronghold is paramount. Explore the following guidelines to enhance your defense against the menacing threat of ransomware.
Keep Your Castle Updated:
Regularly update your software, including the operating system, applications, and programs. These updates often harbor security patches, shielding you from known vulnerabilities that ransomware can exploit.
Arm Yourself with Antivirus and Antimalware:
Install and consistently update robust security software. Conduct regular system scans for potential threats and ensure your virus definitions are up-to-date.
Fortify with Data Backups:
Implement a routine backup strategy for crucial files, storing them on an external device or in the cloud. This precautionary measure allows for swift data restoration in the event of a ransomware attack.
Navigate Emails with Caution:
Exercise vigilance with emails and links. Avoid clicking on links or downloading attachments from unknown or suspicious sources, as ransomware often infiltrates through phishing emails.
Limit User Privileges:
Reduce the impact of potential attacks by refraining from using administrator accounts for daily tasks. Opt for standard user accounts to restrict unwarranted access.
Fortify Your Digital Perimeter:
Enable your firewall and configure filtering rules to block unauthorized connections. Implementing filtering rules can effectively limit network traffic, enhancing your overall cybersecurity.
Disconnect External Storage Devices:
When not in use, disconnect external storage devices such as USB drives or external hard disks. Ransomware can encrypt files on connected devices, making this a crucial preventive measure.
Explore Advanced Security Solutions:
Delve into advanced security solutions designed to combat ransomware specifically. Research and consider integrating these solutions for an extra layer of protection.
By incorporating these practices into your cybersecurity regimen, you can fortify your defenses and navigate the digital realm with confidence, keeping GhostLocker and other cyber threats at bay.
Unmasking GhostLocker: Indentifying Compromise with Indicators of Compromise (IOC)
In the intricate world of cybersecurity, Indicators of Compromise (IOCs), offering insights into the potential presence of malicious activities. Below, we present specific IOCs tailored for GhostLocker and its formidable variant, GhostLocker 2.0.
GhostLocker key Indicators of Compromise:

- Unusual File Extensions: Look for files carrying the “.ghost” extension. The presence of this extension signals potential encryption by GhostLocker, urging heightened scrutiny.
- Ransom Messages: A screen displaying a demand for cryptocurrency payment to decrypt files is a strong indicator of a ransomware attack. Pay close attention to any such ransom messages.
- Altered File Names: This ransomware often alters file names, adding strange characters. Stay vigilant for unexpected changes in file names, as they may indicate encryption.
- System Logs Analysis: Scrutinize system logs for unusual activities or connections to unknown servers. Events linked to GhostLocker may leave traces in system logs, aiding in early detection.
- System Slowdowns: An unexplained slowdown in system performance could be a sign of ransomware infection. Monitor your computer’s speed for any significant changes.
- Access Restrictions: Difficulty accessing specific files or applications may indicate GhostLocker’s presence. Investigate any disruptions in file or program accessibility.
- Communication with Malicious Domains: Employ security tools to monitor your system’s communication with suspicious or malicious domains. Uncover any unauthorized connections that may point to GhostLocker activity.
- Anomalies in Network Traffic: Keep an eye out for abnormal spikes in network traffic or outgoing connections to unfamiliar IP addresses. GhostLocker may manifest itself through unusual patterns in network behavior.
Remember, these indicators are not foolproof, but they serve as valuable tools in detecting the potential presence of Ghost Locker or its advanced iteration, Ghost Locker 2.0.