The OWASP Top 10 is a standard awareness document for developers and web application security. It represents a broad consensus about the most critical security risks to web applications.
The inception of the Open Web Application Security Project (OWASP) dates back to September 9, 2001, establishing itself as a non-profit entity dedicated to enhancing the security of software. With an overarching goal of facilitating the accessibility of content and tools, OWASP initially concentrated on web-centric applications, as implied by its name. However, its purview has evolved over time, extending to encompass diverse domains, including the realm of mobile applications.
OWASP top 10 vulnerabilities
The OWASP Top 10 represents a widely acknowledged compilation of the foremost 10 vulnerabilities inherent in web applications. Serving as a benchmark awareness document for developers and security practitioners, its inaugural release occurred in 2003, with subsequent updates every three years initially, transitioning to a four-year cycle post-2013. The 2021 iteration marks the eighth publication of this list by OWASP.
As an invaluable resource, the OWASP Top 10 offers a foundational entry point for individuals with limited exposure to cybersecurity, particularly within the domain of application security. It aids in determining the priority of vulnerabilities, enabling those overseeing the development, testing, and deployment of applications to enhance security measures and mitigate potential risks to their organizations.
Given its widespread adoption, the OWASP Top 10 has evolved into the de facto standard for application security. It serves as a reference point in various security-related materials, including training content, standards, reports, and tools.
Top 10 web application security risks
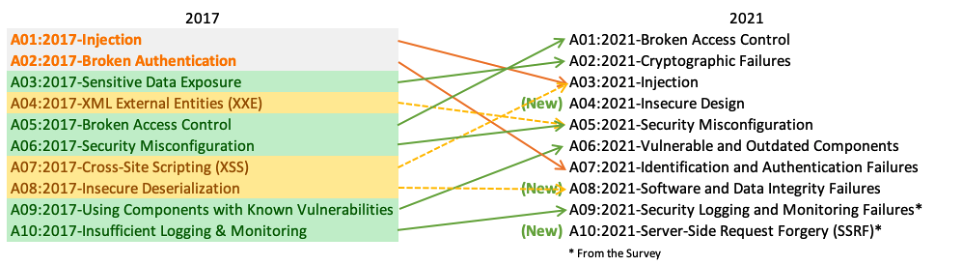
In the OWASP Top 10 for 2021, noteworthy shifts and introductions are observed across various vulnerability categories:
- 2021-Broken Access Control:
- Advances to the top spot from the fifth position.
- 94% of applications underwent testing for broken access control, with the highest occurrences among the 34 Common Weakness Enumerations (CWEs) associated with this category.
- 2021-Cryptographic Failures:
- Climbs to the second position, previously labeled as Sensitive Data Exposure.
- Emphasizes failures linked to cryptography, often resulting in sensitive data exposure or system compromise.
- 2021-Injection:
- Descends to the third position, with 94% of applications tested for injection vulnerabilities.
- The category now includes Cross-site Scripting (XSS) in this edition.
- 2021-Insecure Design:
- Introduced as a new category in 2021, focusing on risks associated with design flaws.
- Advocates for increased utilization of threat modeling, secure design patterns, and reference architectures.
- 2021-Security Misconfiguration:
- Rises from the sixth to the fifth position.
- 90% of applications were tested for misconfigurations, aligning with the prevalence of highly configurable software.
- 2021-Vulnerable and Outdated Components:
- Formerly titled Using Components with Known Vulnerabilities, it secures the sixth position.
- Notably, it lacks Common Vulnerability and Exposures (CVEs) mapped to included CWEs, necessitating default exploit and impact weights.
- 2021-Identification and Authentication Failures:
- Formerly Broken Authentication, it slips to the third position.
- Encompasses CWEs more related to identification failures, reflecting the impact of standardized frameworks.
- 2021-Software and Data Integrity Failures:
- Emerges as a new category, emphasizing assumptions related to software updates, critical data, and CI/CD pipelines without integrity verification.
- Incorporates Insecure Deserialization from 2017 within this expanded category.
- 2021-Security Logging and Monitoring Failures:
- Formerly Insufficient Logging & Monitoring, it ascends from the tenth position.
- Expanded to include various types of failures, challenging to test for, and essential for impacting visibility, incident alerting, and forensics
- 2021-Server-Side Request Forgery:
- Added based on the Top 10 community survey, securing the tenth position.
- Exhibits a relatively low incidence rate but boasts above-average testing coverage, along with high ratings for exploit and impact potential, indicating its significance as per the security community’s perspective.